Setup on Shield
Important
This guide is only for Turris Shield. If you want to set up another Turris device (Omnia, MOX or Turris 1.x) please use the appropriate guide.
Turris Sentinel is enabled by default on Shield firewalls. We strongly encourage to keep it enabled because it helps to protect all Sentinel users against security threats. But if you don’t want use it for some reason you can disable it.
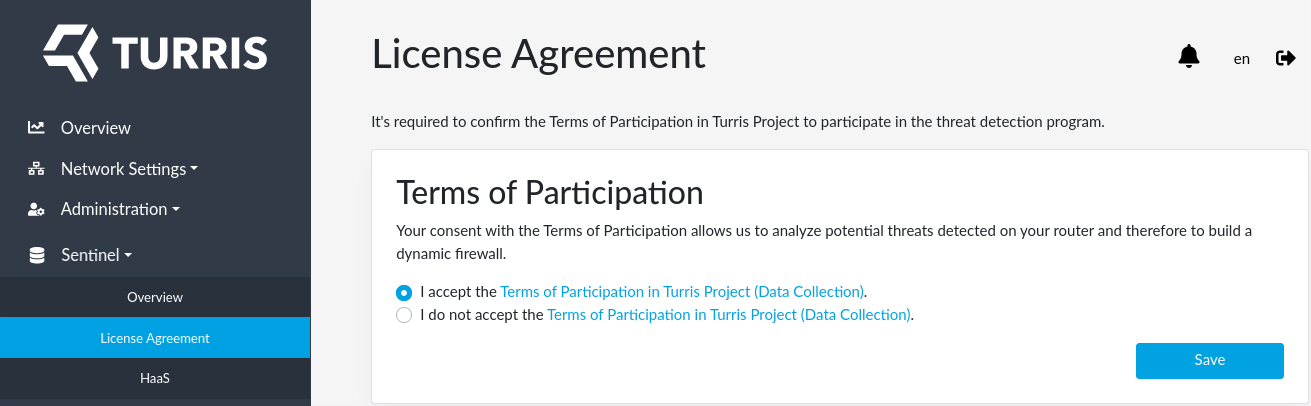
The only thing you have to do is to disagree with our EULA. You can find it at the Sentinel -> License Agreement tab in reForis. Switch the radio button to I do not accept… and press Save.
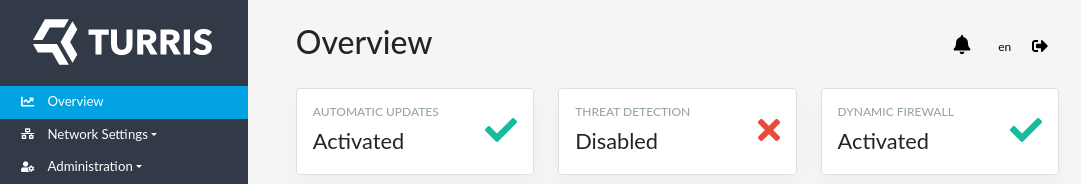
When done, you can see at the Overview page that threat detection is disabled.
If you wish to continue using Sentinel, you still have few options to configure. Notably you can select which threat detection tools you want to use or you can install HaaS which is not configured by default.
Choose which threat detection tools to use⚓︎
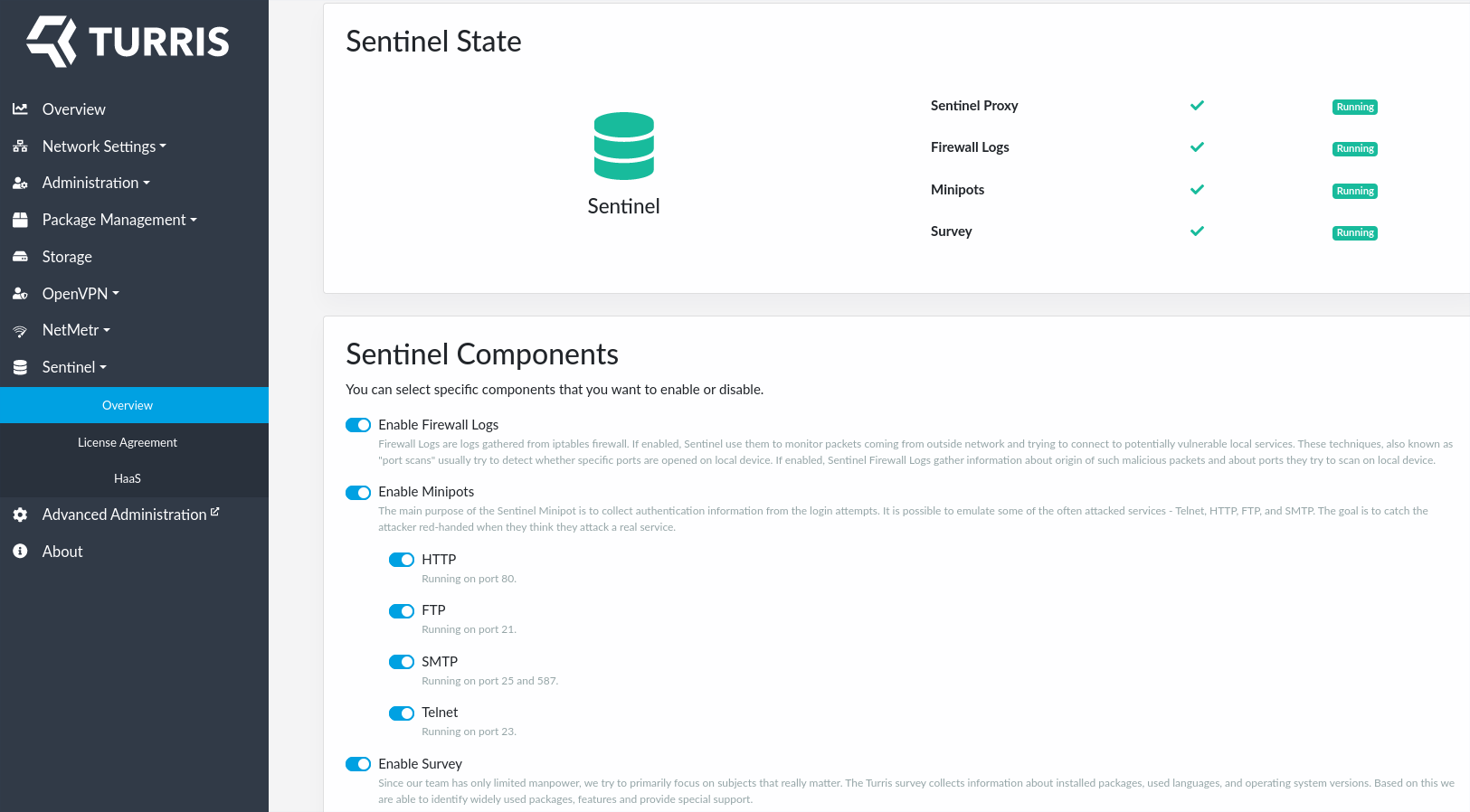
With Sentinel installed and EULA approved your Sentinel Overview tab will shine green.
In Sentinel overview tab you can see which locally run Sentinel threat detection tools are enabled and running. Here, you can also disable or enable only a subset of them.
HaaS⚓︎
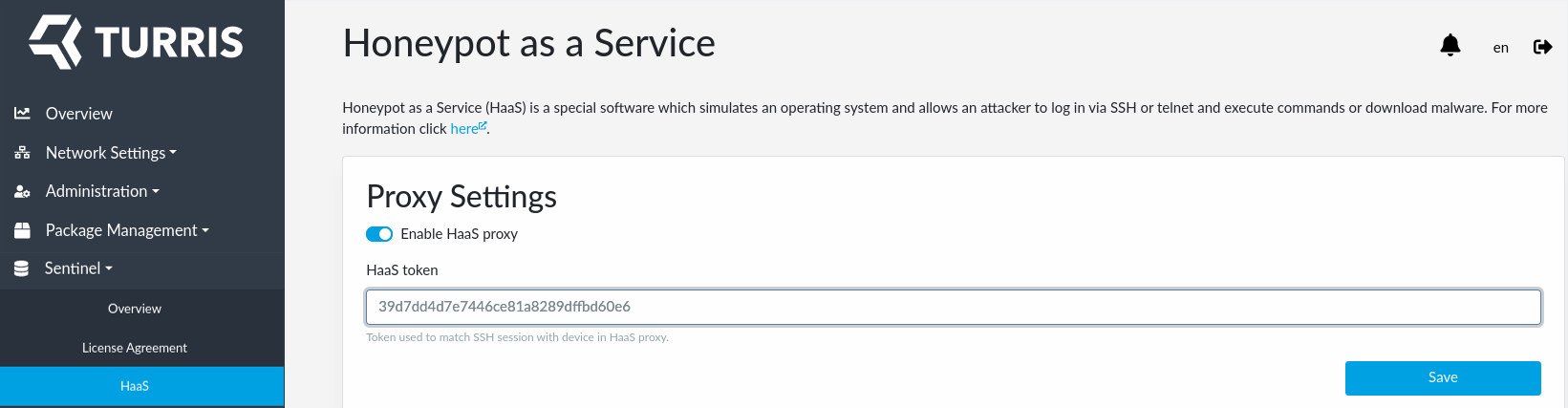
Besides the tools listed in Sentinel overview tab, you are also free to use HaaS. HaaS is not listed there because it’s setup requires one more step which requires registration in a separate website and obtaining a HaaS token as described in a separate guide. HaaS also do not collect data on you router and therefore nor EULA approval nor running Sentinel proxy is needed.
Once you have you HaaS token with you, fill it in using Sentinel HaaS tab in reForis:
Important note about Internet Service Providers⚓︎
Some Internet Service Providers (ISPs) actively detect potentially vulnerable services running by their customers. If they find such services they send notification or even block external access to such ports.
Info
The same applies for some community, municipal or other networks as well.
Some parts of Sentinel (Minipots and HaaS) may be identified as such vulnerable services because they pretend to be vulnerable so that they are able to lure potential attackers (with no risk since the attackers do not enter any real environment).
What to say to your ISP if you receive such warning:
- Those services are operated intentionally as a part of the Sentinel security research project.
- They are provided by honeypots and not vulnerable software.
- The results of the project are instantly deployed to routers and improve security of the routers and the networks beyond them.
- You want to keep those ports/service accessible from the Internet.
Please let us to know (tech.support@turris.cz) if your ISP sends you such warning or event applies some “protective” measures on your Internet connection.
Warning
Some ISPs silently block access to some ports (they do not declare that they do so). It is useful to ask explicitly which ports are blocked.